
The global technology and finance sectors run on the promise of seamless access. We rely on systems like the Identity Provider or IdP to be the single source of truth for every employee customer and partner ensuring security and efficiency. This critical system allows millions of users to access vast resources across multiple service providers with a single login.
Yet this foundational security layer carries a catastrophic risk.
One major Fortune 500 company recently discovered this risk when their entire operation came to an abrupt halt. The cause was not a complex external hack or a sophisticated phishing campaign. It was an internal error a seemingly minor IdP misconfiguration that spiralled into system paralysis costing the enterprise millions per hour in lost revenue and incurring immediate regulatory scrutiny.
How could one small administrative tweak to a federated access system bring down a colossal entity?
In this case study we unpack the anatomy of this severe failure. We analyse the critical error that occurred the scope of the resulting disaster and the three non negotiable lessons that every technology leader must adopt to fortify their own identity perimeter. This is a story about the absolute necessity of expert IdP governance.
The Anatomy of the Misconfiguration: The Critical Error
At the core of the outage was the company s Identity Provider. The IdP is a mission critical piece of infrastructure acting as the central gatekeeper in a federated access model. It performs the vital function of authenticating users and issuing security assertions to various connected Service Providers or SPs like cloud applications CRMs and internal tools.
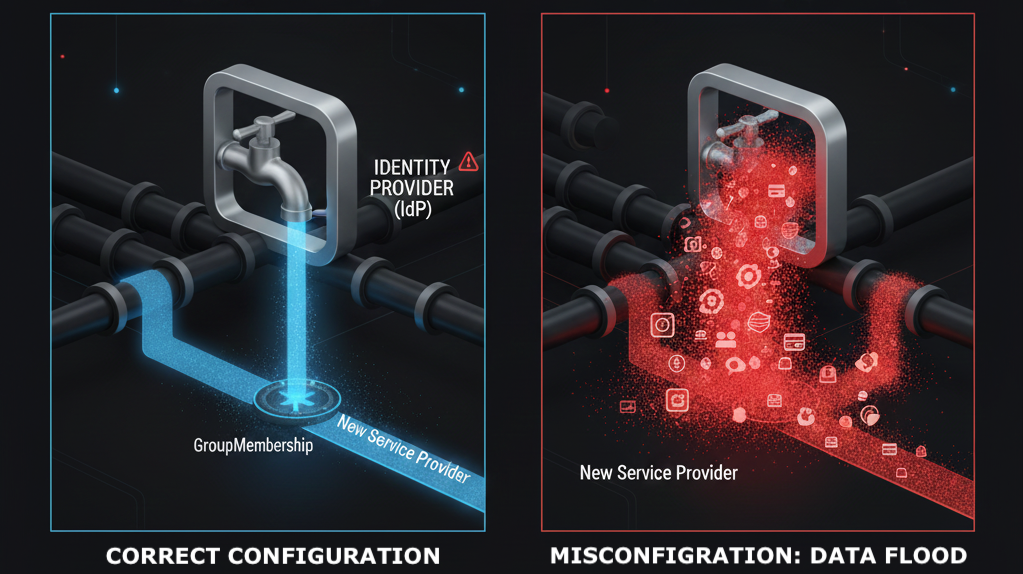
The Fortune 500 in question used a highly customised Shibboleth IdP deployment to manage complex enterprise scale access rules across thousands of SPs globally. The error occurred during a routine deployment of a new corporate application which required an update to the IdP s Attribute Release Policies.
The administrator intended to configure the policy to release a single non sensitive attribute GroupMembership to the new SP. However due to a critical oversight in the configuration file combined with an inadequate validation process the policy was not restricted to the target SP.
Instead of only releasing data to the new application the faulty rule accidentally triggered a global attribute release for all users on all connected Service Providers. Crucially the attribute released was not just GroupMembership but a comprehensive set of sensitive data attributes including PII and internal roles which should never have left the secured zone.
The ripple effect was immediate and catastrophic. Every application that requested authentication from the IdP suddenly received highly sensitive information for all users causing immediate system instability security alerts and eventually a mandated shutdown of the entire access environment to prevent further compliance breaches. A single administrative error turned the IdP from a gatekeeper into an unrestricted data faucet.
The Catastrophic Impact: Beyond the Technical Outage
The immediate technical fix was complex but the damage was already done. The impact went far beyond a simple outage demonstrating the true stakes of IdP security and governance.
The Business Paralysis was immediate. As all employee access was shut down financial transactions ceased logistics chains froze and crucial customer support systems went offline. Estimates placed the financial loss at well over a million dollars for every hour the system was down resulting from lost productivity and failed transactions.
The greater crisis was Security and Compliance. The accidental release of Personally Identifiable Information PII and internal access roles represented a severe breach of data security protocols. This triggered mandatory disclosure requirements under various global regulations. The company faced massive fines and class action lawsuits a direct result of the failure to correctly govern its access system.
This case study proves that the security integrity and availability of the IdP infrastructure is directly proportional to the operational resilience of the entire business. Investment in robust governance and expert support is not an IT cost it is a business insurance policy.
Three Non Negotiable Takeaways
The post mortem following the Fortune 500 failure revealed systemic gaps in identity governance and deployment processes. For any organisation relying on a complex IdP like Shibboleth or Azure AD to manage federated access these three lessons are essential to preventing a similar catastrophe.
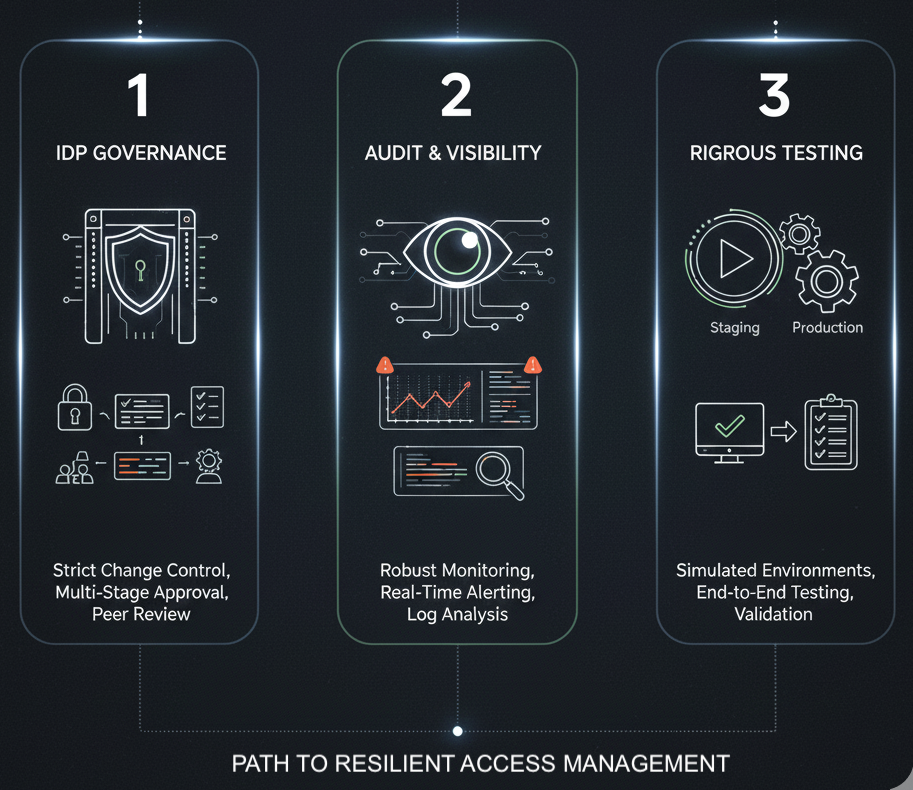
Lesson 1: IdP Governance Must Be a Top Tier Priority
Configuration changes to the Identity Provider cannot be treated as a simple administrative task. They are highly privileged operations with the potential to affect every single user and application across the enterprise. Establishing strict change control that requires multi stage authorisation peer review and documented justification for every single modification is non negotiable. IdP policies must be treated with the same criticality as firewall or network routing rules.
Lesson 2: Audit and Visibility are Essential
A primary factor in the IdP s failure was the delay between the misconfiguration occurring and the security team accurately diagnosing the cause. You cannot fix what you cannot analyse. Implementing robust monitoring and logging across the IdP infrastructure is mandatory. This includes real time alerting on anomalous behaviour unusual attribute releases or sudden spikes in authentication failures. Expert logging ensures that a delay in detection does not become a failure in containment.
Lesson 3: Testing is Not Optional
The misconfiguration only became a global disaster because it was deployed directly to the production environment. Configuration updates must first be deployed and tested in a staging or development environment that accurately simulates the live production infrastructure. This includes end to end testing of the authentication process across a representative sample of all connected Service Providers. If testing is skipped for the sake of speed you are trading short term convenience for the risk of existential business failure.
Key takeaways: The Path to Resilient Access Management
The case of the Fortune 500 company serves as a stark reminder that in the world of federated access the weakest link is often a misconfigured Identity Provider. IdP governance is the ultimate defence against operational paralysis compliance breaches and catastrophic financial loss. Securing the perimeter is no longer enough the identity core must be robust secure and expertly maintained.
To protect your organisation from the failures outlined in this case study you require more than just software you need proven expertise and a partner who understands the intricate complexities of Shibboleth Azure AD and ADFS deployments.
Fortifying Your Identity Perimeter
The team at Overt Software Solutions specialises in delivering that expertise. We provide comprehensive IdP governance audits migration support and 24/7 managed services ensuring your identity infrastructure operates with absolute security and resilience. Do not wait for a single misconfiguration to become your organisations next headline disaster.
Contact Overt Software Solutions today to secure your federated access environment with industry leading professionals.
