STEM education—Science, Technology, Engineering, and Mathematics—sits at the heart of innovation. From coding labs to cloud-based research, today’s classrooms and universities are more dependent on technology than ever. This shift has unlocked new opportunities for collaboration and discovery, but it has also introduced a growing vulnerability: the digital environment is now a primary target for cyberattacks.
In the UK, reports continue to show that cybersecurity in education is a pressing concern. Institutions across all levels face an increasing number of phishing attempts, ransomware incidents, and breaches of student records. For STEM programmes, where experiments, data, and projects often rely on online systems, the consequences of an attack can be especially severe.
Building STEM education cybersecurity into everyday practice is not just a safeguard against disruption—it is a foundation for trust. When systems are secure, students and staff can focus fully on their work, confident that research data and personal information are handled responsibly.
This is where Overt Software Solutions provides support. With expertise in Single Sign-On (SSO), Multi-Factor Authentication (MFA), and federated access management, we make it easier for schools and universities to strengthen their defences without making life harder for the people who use those systems.
In this blog, we will look at the evolving threats that STEM educators face, share real case studies, and explore how institutions can create a strong cybersecurity foundation for the future.
The Cyber Threat Landscape in STEM Education
The growth of digital tools in STEM has transformed how students and researchers learn, collaborate, and innovate. But this same reliance on technology has created more opportunities for cybercriminals. Education is now one of the most frequently targeted sectors, and STEM programmes face unique risks because of the sensitive nature of the work they carry out.

Recent findings from the UK Cyber Security Breaches Survey highlight the scale of the challenge. Universities and further education colleges report frequent attempts to compromise their systems, and many have invested in risk assessments to stay ahead of attacks. In contrast, schools often lack the same level of cybersecurity maturity, leaving them more exposed. This gap matters because STEM learning increasingly begins at an early stage, and weak defences in one part of the education system can have long-lasting consequences.
The threats themselves are varied. Phishing emails disguised as official messages continue to slip into inboxes, and ransomware remains a constant danger. There are also risks tied to the digital tools used in STEM. Online laboratories, cloud storage for student projects, and remote access to specialist software can all become points of entry if they are not properly secured. When attackers gain access, the damage extends far beyond temporary disruption. Student privacy is at stake, and research results can be corrupted or even stolen.
This evolving landscape makes one thing clear: without strong protections in place, the digital infrastructure that supports STEM learning is vulnerable. The next step for education leaders is to ensure that cybersecurity is treated not as an afterthought but as a foundation that supports every experiment, assignment, and innovation.
Case Studies from Education Institutions
Real-world examples show why a strong cybersecurity foundation is essential for STEM education. The following cases highlight both the challenges and the progress being made across the sector:
Universities Under Pressure
Research from a group of UK universities found that while students in computing and engineering programmes were learning about cybersecurity in the classroom, the wider institutional systems were struggling against phishing and malware attacks. The mismatch between what was being taught and how systems were secured revealed the need for stronger, organisation-wide protections.
Resource: Challenges and Opportunities of Teaching Cybersecurity in UK Universities (Abertay University study).
Breaches in Colleges and Universities
The UK Cyber Security Breaches Survey 2025 reported that higher education institutions and further education colleges remain among the most frequent targets of cyberattacks. Many have introduced risk assessments and monitoring to strengthen their defences. However, the survey also found that schools often lag behind in cyber maturity, leaving a gap that can affect STEM learning from the earliest stages.
Resource: UK Government Cyber Security Breaches Survey 2025 (Education Findings).
Embedding Cybersecurity in Practice
Some institutions have taken proactive steps by weaving cybersecurity into daily operations. One example is the integration of incident response planning into teaching programmes, giving both staff and students hands-on experience in recognising and responding to threats. Others have centralised access management so administrators can quickly shut down compromised accounts and limit the damage from an attack.
Resource: UK Case Study on Cybersecurity Education and Accreditation (Northumbria University).
Building the Foundations: Key Elements for STEM Cybersecurity
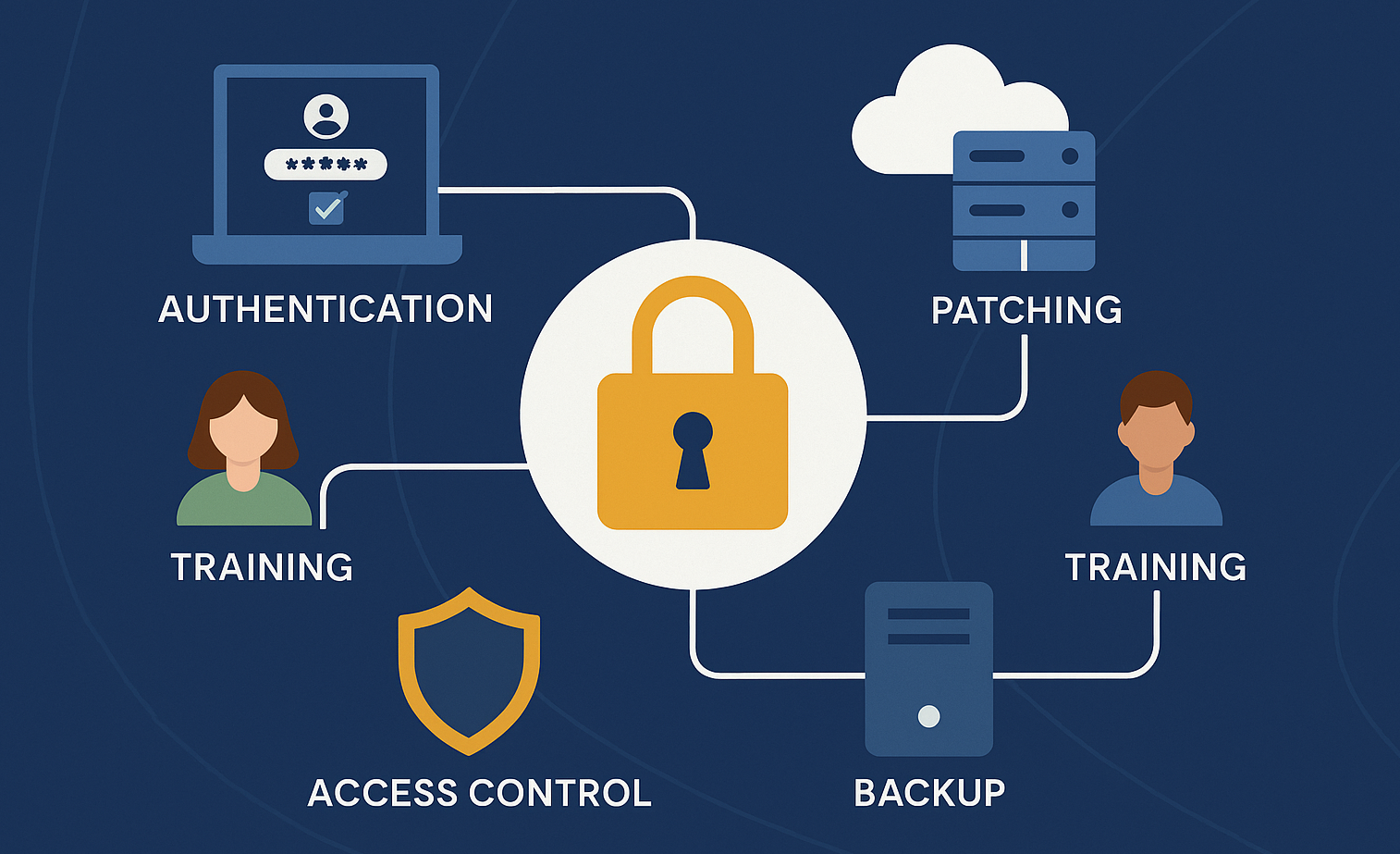
A strong cybersecurity foundation in STEM education depends on a combination of technical safeguards, practical processes, and cultural awareness. Each of these elements reinforces the others, creating a secure environment where teaching and research can thrive.
Secure Authentication
One of the most important defences for STEM institutions is making sure that logins cannot be easily compromised. With so many platforms in use—virtual labs, research portals, and cloud storage—it only takes a single weak password to put an entire department at risk. Multi-Factor Authentication (MFA) and Single Sign-On (SSO) reduce this risk while keeping the login experience simple for students and staff.
Access Control and Privilege Management
STEM environments often involve a wide range of users: teachers, researchers, students, and visiting staff. Not everyone needs the same level of access. Strong access control policies make sure people can only reach the systems and data relevant to them. By using federated access management, institutions can enforce these rules consistently.
Regular Risk Reviews and Patching
The tools used in STEM education—from learning management systems to specialist software—are frequently updated. If those updates are not applied on time, vulnerabilities can remain open for attackers. Routine risk reviews help identify where gaps exist, and patch management ensures those gaps are closed quickly.
Awareness and Training
Technology alone cannot solve every problem. People are often the first line of defence. In STEM programmes, where students and staff handle data, code, and connected devices, awareness of cybersecurity risks is essential. Training programmes and clear communication help build a culture where secure behaviour becomes second nature.
Backup and Recovery
Even with strong defences, incidents can still happen. When they do, the ability to recover quickly makes the difference between a minor setback and a major crisis. Reliable backup strategies safeguard research data, coursework, and institutional records.
Together, these elements form the backbone of a resilient cybersecurity strategy for STEM education. When implemented consistently, they give institutions the confidence to innovate while keeping their communities safe.
Overcoming Barriers in STEM Cybersecurity
Barrier | Why It’s a Challenge | Practical Ways Forward |
Budget Limitations | With limited funds, cybersecurity investment often takes a back seat to visible teaching resources. The result is higher long-term risk if prevention is ignored. | Scalable solutions such as Multi-Factor Authentication (MFA) and Single Sign-On (SSO) provide strong defences without unnecessary expense. |
Legacy Systems and Disparate Tools | STEM environments rely on a mix of modern cloud services and older, specialised systems. This patchwork makes consistent security difficult. | Federated access management can centralise authentication across both old and new platforms, closing the gaps that attackers target. |
Skills Gap | Educators and researchers are experts in their fields but may not have deep cybersecurity knowledge. Small IT teams can’t always cover the gap. | Institutions benefit from clear guidance and support, ensuring staff can adopt safer practices while IT teams focus on core responsibilities. |
Resistance to Change | New security measures are often seen as disruptive, with users frustrated by extra steps in login processes. | Tools like SSO simplify access by reducing the number of passwords to remember, making stronger security feel like a convenience rather than a burden. |
Why Overt is the Right Partner for STEM Cybersecurity
Building a strong cybersecurity foundation requires more than just technology. It demands solutions that fit the unique environment of education, alongside guidance that helps institutions put those solutions into practice. This is where Overt Software Solutions has earned trust across the sector.
Here’s how our services align with the needs of STEM education:
- Secure authentication through SSO and MFA helps institutions protect accounts without placing extra burdens on staff and students.
- Federated access management ensures administrators can control who has access to different systems, reducing the risk of misuse.
- Regular patching, monitoring, and backup strategies strengthen resilience and keep learning and research running smoothly even when issues occur.
What sets Overt apart is the way these services are delivered. Support does not stop at installation — we continue to work with institutions to refine policies, build awareness among staff and students, and adapt to new challenges as they emerge. For education providers preparing the next generation of scientists, engineers, and innovators, this partnership approach ensures cybersecurity becomes part of a sustainable foundation for growth.
The Key Takeaways
STEM education is shaping the future of innovation, but that future depends on more than creativity and technical skill. Without strong cybersecurity, even the most advanced learning environments remain vulnerable to disruption. The lessons from real-world institutions show the risks clearly: phishing attacks, ransomware, and weak access controls can undermine teaching, research, and student trust.
By treating cybersecurity as a foundation rather than an afterthought, schools, colleges, and universities create safer spaces for discovery. Secure authentication, clear access policies, timely updates, and resilient recovery plans all contribute to an environment where staff and students can focus on their work with confidence.
Overt Software Solutions supports education providers in building that foundation. Through our expertise in authentication, access management, and long-term support, we help institutions strengthen their defences in ways that are practical, sustainable, and future-ready.

