Malware-as-a-service (MaaS), has become popular because it is powerful, instantly ready to use and requires no technical skills. Similar to the term “software as a service” (SaaS) revenue model, MaaS offers malware services and products and as a result, enables “customers” to easily distribute malware.
How does Malware-as-a-Service (MaaS) work?
MaaS is similar to SaaS (Software-as-a-Service), as with any other web service you can buy it over the Internet (rumours suggest hackers typically purchase these services from the dark web). However, unlike SaaS, MaaS, developers supply the “customer” with a complete malware instructions kit; receiving guidance on managing the malicious software and what specific steps are required to initiate an attack.
This means that there is no need for the “customer” to have any programming knowledge. MaaS “customers” can benefit and make money through cybercrime without needing advanced technical knowledge or skills.
“Customers” are increasingly using MaaS platforms to conduct cyberattacks, paying the owners of the MaaS a subscription fee in order to do so. The providers of these platforms are not interested in the data that is stolen through their product—they may sell it to the highest bidder on Dark Web forums or leave it with the MaaS subscriptionists.
What does Malware-as-a-Service (MaaS) Provide?
Similar to legal businesses, these MaaS companies use marketing strategies such as websites and paid ads to advertise their range of products and services to potential “customers”. Below are a few examples of the different types of malware services they provide;
Off-the-Shelf attacks
Depending on which attack type you prefer, many different attack types are available to choose from, including ransomware, phishing emails, banking trojans, computer worms and adware.
Targeted Attack
When a “customer” wishes to receive private information from a specific business, these MaaS companies will act as cyber-assassins to attack their “customers” specified target. These targeted cyber-attacks will include social engineering tactics such as whaling and spear phishing.
“Customer” support
Many service providers (legitimate or not) wish to ensure that their customers see the value in their products. The MaaS industry is no different, and will often supply their “customers” with analytical guidance, for example, informing their customers on the best time they should send their phishing email to get the most clicks and malware downloads.
Victim aftercare
These companies are also service conscious toward their victims; once an organisation’s data has been stolen or network infiltrated, MaaS providers will sometimes provide the user with tips on how to better protect themselves in the future, and even take the time to explain bitcoin usage via specially set up chat windows.
Why is it difficult to stop Malware-as-a-Service (MaaS)?
Malware authors use darknet services to hide their command and control servers. Most ransomware today relies on hidden services in the Tor network (The Onion Routing Network) for transaction infrastructure.
Tor, short for The Onion Routing project, is a worldwide network that enables anonymous web browsing. The Tor computer network is based on secure and encrypted protocols to protect users’ online privacy. It uses a layered approach that resembles the layers of an onion.
Although the Tor network has many legal uses, in the Tor network it is also easy to find hidden services that offer malware and other malicious services to their visitors.
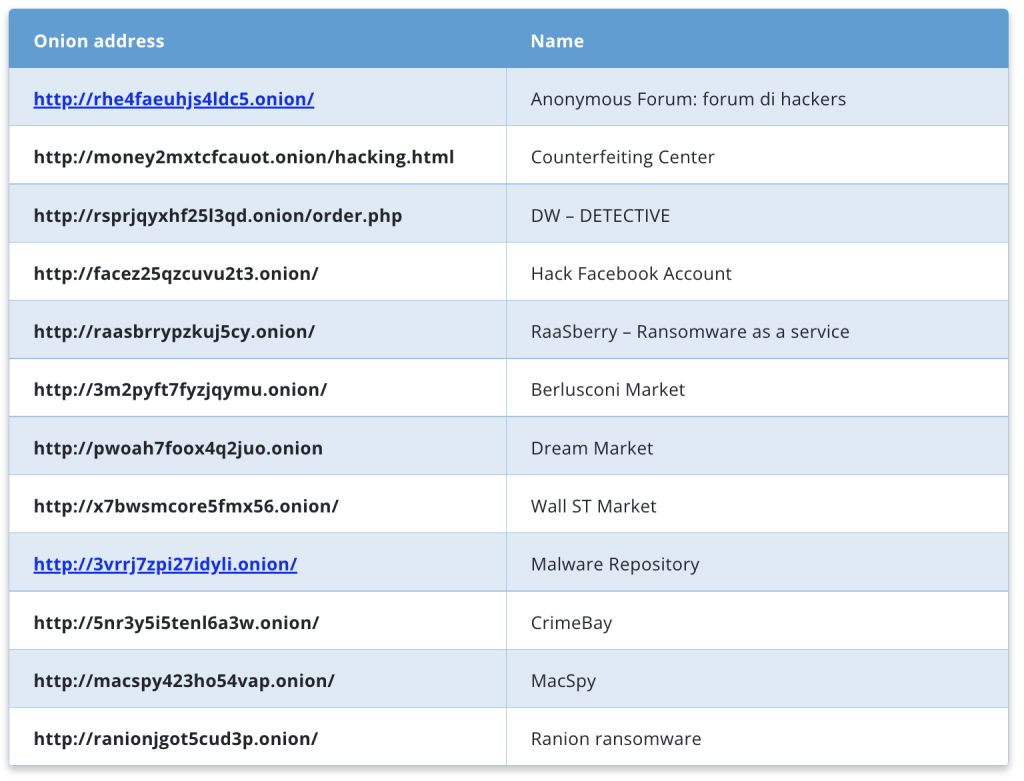
Based on research conducted by Infosec Institute, Many types of malware are controlled by servers directly hosted on Tor and I2P. Malware authors use hidden services to make their botnets resistant to operations run by law enforcement and security firms.
Below is a list of onion sites found by Infosec Institute that were once used by malware authors but are no longer frequented by such people.
How to protect yourself from Malware-as-a-Service (MaaS)?
The cybersecurity industry is constantly evolving so that they can stay ahead of any new malicious software, however, leaving your digital safety to an invisible shield can seem scary. Luckily, there are ways for you to proactively protect your own data from being compromised by malware. The following points can be helpful in protecting yourself and your organisation from hackers:
Patch Management: Keeping your system up-to-date
To protect against Malware as a Service, organisations should ensure that their computers do not contain exploitable vulnerabilities. Having good patch management processes in place reduces the window during which an attacker could potentially exploit them to attack the organisation.
A strong password is the first line of defence in protecting your online accounts from being hacked. If you are using weak passwords or even worse the same weak password for multiple accounts, your passwords could be easily guessed by cyber-frauds within hours. Such practices place you at risk for identity theft and extortion.
Avoiding pop-ups
Some pop-ups are legitimate, but clicking on others can initiate a download of malware or a virus. Some pop-ups even claim your computer is infected with a virus. They may tell you that you need to download software to clean your computer operating system from viruses. That software will in fact be a virus or dangerous malware.
Being cautious about phishing emails
Phishing is the act of sending fraudulent emails or making phone calls in an attempt to obtain sensitive information such as your private account information, password, or credit card information. The messages typically include a link to what appears to be a legitimate website where you’re asked to give your private account information or asked to download malware. For tips on how to recognise phishing attempts please read our blog ‘Phishing Scam: 6 common types and how to avoid them’.
Use strong anti-virus programs
Organisations need to have a strong antivirus installed on all of their computers and ensure that it is scanning and updating regularly. If a computer were infected with malware via a malware-as-a-service botnet, the antivirus could detect and block the malware, minimizing the impact of the attack.
Malicious software is not always created for computers. Mobile phones are also at risk. To protect your phone from malicious software (MaaS), you need to avoid downloading apps from sources other than Google Play or the App Store. Be careful about unknown links in SMS and emails.
Be on the look-out for potential attacks!
Cyber-attacks have become much more complex than they were before. MaaS make use of botnets, which makes cyber-attacks more complex than they were before. As a result, because a data breach can cause a system to collapse, attackers appear to have an advantage in cyber warfare.
Effective cybersecurity measures require a tailored strategy. It is important to consider all possible ways that an intruder can gain access to a system as a security team cannot protect against an attack unless it knows about their systems vulnerability points.
In order to strengthen and protect the organisation’s assets in the face of an ever-expanding threat environment, effective vulnerability management is crucial because it allows security teams to swiftly detect and repair vulnerabilities that aren’t protected by security measures and could be exploited.
One of the most common exploits that hackers take advantage of are people, as such, cybersecurity is not just the responsibility of the Cybersecurity team but the responsibility of all users. Catching a cyber-attack before it has the chance to infiltrate your organisation’s device or network is always the best protection. Don’t forget, as a human firewall users are the first line of defence.
