What is a Computer Virus and How Does it Actually Work?
A virus is a type of malicious software that operates in a particular way, distinguishing them from other types of malware like spyware and adware. Viruses are programs that have been purposefully designed to replicate themselves and spread from one computer to another. They are typically written in a way that makes them difficult for antivirus software or other security software to detect. There are many types of computer viruses that include worms, trojans, spyware and ransomware. There are a couple different methods in which each virus can cause destruction.
- First method – infecting programs. This technique involved inserting their code into other programs so that it can execute when someone uses the app. This can cause a number of problems, such as slowing down computers or crashing them, which is why it’s important to keep all software updated.
- Secondly method – Self-replicating. Viruses spread by replicating in computers and taking over the infected systems.
Not all types of malware are viruses
Computer viruses have been around for a long time, but it’s only in recent years that people really started to take notice of them. In fact, the word “virus” itself is derived from the Latin word that means “to infect.”
According to PRR Computers, Viruses are the most common type of malicious software, with 57% of all malicious software being created by viruses. This means that out of the total number of malicious cyber attacks that have been done, the rest of the remaining attacks are not considered a “Virus”.
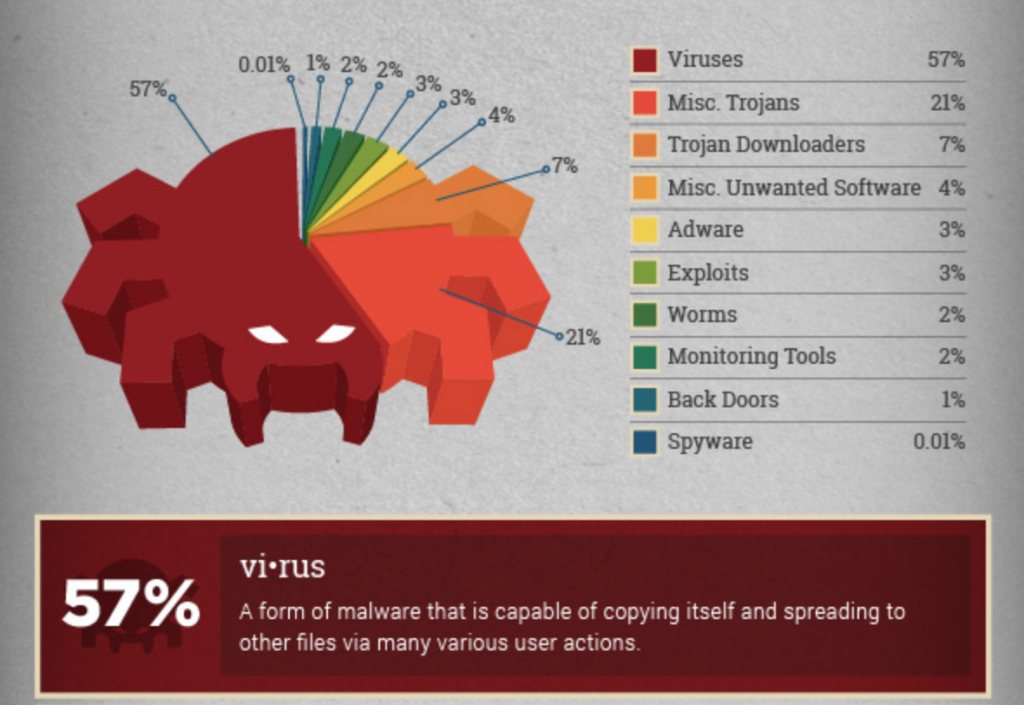
A piece of code that is designed to cause destruction is called “MALWARE”. This can refer to other potentially dangerous types of code. However, Keyloggers, Adware, Trojans, Ransomware, etc are considered amongst the malicious software toolkit (malware) of the 43%.
Whenever you hear someone mention the word “cyber attack” or “scary malware statistics”, remember that they’re not always caused by viruses.
Malware and Virus difference
|
VIRUS |
MALWARE |
|
Name adopted from a metaphor of the biological “virus” that attacks the human’s immune system. |
Malware is the short name for “Malicious” “Hardware” |
|
A code of software that self-replicates to infect programs. |
A computer code that infects machines and executes an unknown program to the victim’s computer. |
|
A hacker can place a dummy app in the victim’s computer desktop. But it needs the victim to trigger the “dummy app” in order for the virus to start its dirty job. |
Able to automatically execute malicious programs within the system’s startup. (No trigger is needed). |
|
Most common Virus: Worm, SQL slammer, ILOVEYOU, Tinba, Conficker, Nimda, etc |
Most common Malware: Adware, Trojans, Bots, Ransomware, Spyware, etc |
Viruses Need a Trigger to Activate
Due to how people often use the terms. In most cases, Viruses are often misunderstood as malware. In reality, they are a different type of malware which has a distinct mode of transmission and behavior.
It is possible for programs and computers to get infected with viruses. But in order for a computer virus to work, they need a trigger to activate before they could start doing their dirty jobs. Once someone triggers the virus, things will go downhill very quickly for them as the virus starts to execute its programmed commands.
On the other hand, malware can enter your device on their own and start replicating themselves. They don’t require any action to spread their destructive work.
The conficker worm virus
The most prolific virus of all time is known as the conficker. It targets flaws in the Windows operating system to spread across computer networks while forming its network of auto-acting viruses.
In 2008, the conficker infected millions of computers across 190 countries, including everything from home personal computers to business and government networks. The conficker worm virus plays a great role on VIRUS. because most Virus needs an “inside person” but this conficker virus is disguised as a PDF. so it shocked al ot of people. It is the largest known computer infection on record.
Here is an illustration of how the conficker worm virus spread and infect win32 computers
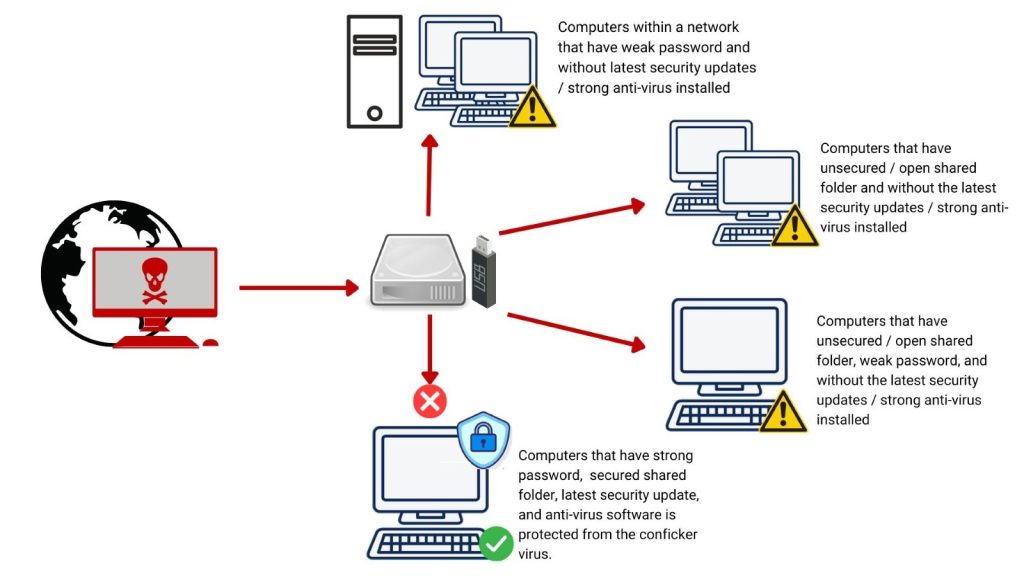
A worm virus known as Conficker takes advantage of a vulnerability in the Microsoft Server service to spread. Computers and servers that are not patched with security update MS08-067 are susceptible to attacks.
If a computer becomes infected with Conficker, it can perform brute-force attacks on other computers in the same network to steal passwords and gain access.
Another way that the Conficker worm spreads is by modifying a file on removable media like USB drives and CDs. Once you plug in your device, a new option will appear on the AutoPlay dialog box. Choosing this option triggers the worm, which then infects your computer.
Largest Virus Scandal: Does Antivirus Create Viruses?
It is not a surprise to see that viruses are used by computer antivirus manufacturers. While some people may think this is just a conspiracy theory, it’s been suggested that they earn billions of dollars due to antivirus programs.
Bill Gates has been falsely accused of this, but the majority of these accusations are simply not true. There are even public threads on Quora that attempt to verify this! These false claims have resulted in some big players defending themselves by writing blog posts in an effort to refute the accusations.
Scareware the reasons for this conspiracy. Scareware is a type of software which tries to scare people into contacting its advertisers. Scareware has advertisements or pop ups that mention your computer could be infected with viruses and tries to convince you into downloading the advertised “free antivirus software.”
Scammers make up fake antivirus software which spreads viruses and other types of malware on your machine. Once the user installs this software, they will notice that their device’s performance starts to deteriorate even more, leading them to believe that these programs contain viruses themselves.
In reality, there is no way an antivirus company would create and spread computer viruses. They are already having a hard time dealing and finding solutions to solve malicious hardware and virus problems. Besides, it’s definitely not worth it to ruin their current standing within a very competitive market.
Take precautions
As most viruses are self-replicating, they can easily spread to other devices and cause damage to your valuable data. That’s why it is important to always keep your programs up-to-date and have a reputable antivirus program installed. Also, be on the lookout for symptoms of computer virus so your computer doesn’t become compromised. Warning signs include:
- Sudden Slow down on the operating system
- Mysteriously moving mouse cursor
- Strange popups and ads displaying
- Unknown websites automatically opening in the browser
- Data mysteriously deleted
- Unknown programs running automatically or installing themselves
Beware of fake antivirus programs! Always use antivirus programs from well-known and reputable companies. People are one of the most common vulnerabilities exploited by cyber attacks. Cybersecurity isn’t just the responsibility of antivirus companies but the responsibility of every user. Catching a cyber attack before it has the chance to infiltrate your device or network is always the best protection. As a human firewall, you’re the first line of defense. .
