Cybercrime encompasses all digital crime that involves computers. This can include using malware and malicious code to spread illegal information or images. The development of the internet world, which is increasingly rapid and is very much needed at this time, has an impact that gives rise to technological geniuses who develop cyber attacks.
Definition of cyber attack
“Cybercrime” is a wide term that refers to criminal activity that targets or uses computers and networks. Most cybercrime is committed by cybercriminals who want to make money. However, occasionally cybercrime is motivated by other reasons—such as political or personal reasons.
Cybercriminals might use malware to damage your computer or stop it from working. Or they could steal or delete your data or prevent you from using a website or network. They might also attack a business by preventing it from providing a software service to its customers – this is called a Denial-of-Service (DoS) attack.
Cyber attack cases
Many attacks occurred after the emergence of business needs for the internet and technology. Here are 6 of the worst cyber attacks that have received the most attention based on the extent of distribution and the resulting threats.
1. WannaCry
Who doesn’t know about the WannaCry ransomware attack? This cyber attack became the biggest in May 2017 and shocked the IT world, especially the antivirus world. WannaCry is a cyber attack that infects computers and encrypts files on the PC’s hard drive.
In May 2017, a large-scale ransomware attack known as WannaCry spread globally through Windows computers. Microsoft had released a security patch for EternalBlue, the exploit that allowed WannaCry to propagate (nearly two months prior ). However, many Windows users had not updated their software or were using out-of-date versions of Windows and so were vulnerable to the attack.
A global ransomware attack infected an estimated 230,000 computers across 150 countries in just hours. Security researcher Marcus Hutchins discovered a “kill switch” that dramatically slowed the attack’s spread.
Here is a screenshot footage from Securelist, showing the WannaCry ransomware in action scamming its victim;

Many factors that made the initial spread of WannaCry so important and famous were the attacks aimed at important systems such as the National Health Service (NHS) in the UK.
Based on the FBI’s Internet Crime Report, reported that complaints about ransomware attacks grew by 20% in the United States in 2020.

Globally, the number of attacks increased by over 60% between 2019 and 2020. Not only are ransomware attacks increasing, but they’re also becoming more prominent.
2. NotPetya ransomware
NotPetya or Petya is the name of the malware that was discovered in 2016. It is inspired by a fictional Soviet satellite from the James Bond film GoldenEye (1995). Petya has an average penetration rate, but its encryption technique is unusual.
The Petya ransomware, disguised as a PDF file, spread through phishing emails. Once activated and given admin access, it would overwrite the Master Boot Record (MBR) to encrypt the hard drive. Files on an infected computer weren’t lost or corrupted; they were simply inaccessible unless the victim paid bitcoins to decrypt them.
In June 2017, a major global cyber attack began targeting Ukrainian companies. On 27 June 2017, Kaspersky Lab reported infections in France, Germany, Italy, Poland, the United Kingdom and the United States. ESET estimated on 28 June 2017 that about 80% of all infections were in Ukraine, with Germany second hardest hit with about 9%.
Here is a screenshot footage from BBC tech, showing the Petya malware infecting a computer PC;

3. Ethereum case
Ethereum is a bitcoin-style cryptocurrency, a peer-to-peer public blockchain network with a digital currency called ether. Cryptocurrencies, like bitcoin, ethereum, litecoin and dogecoin, are virtual or digital currencies that use cryptography to secure their transactions. A blockchain is a public ledger that records all of a cryptocurrency’s transactions.
Ethereum is the world’s computer platform for conducting intelligent contracts between users and ether providers. Ethereum is not the name of a cyber attack but a victim of cyber crime that commits Ethereum theft.
A July 2017 cyber attack targeting Ethereum stole as much as US$150 million from the Ethereum platform in minutes. This raises negative public thoughts about using the ether blockchain on the Ethereum platform.
4. Equifax data breach
Equifax is a data analytics and technology company that helps organisations and individuals make informed personal and business decisions. In July 2017, Equifax data fell victim to a cyber attack that exposed 143 million Americans’ sensitive data by exploiting a vulnerability in the Apache Struts framework.
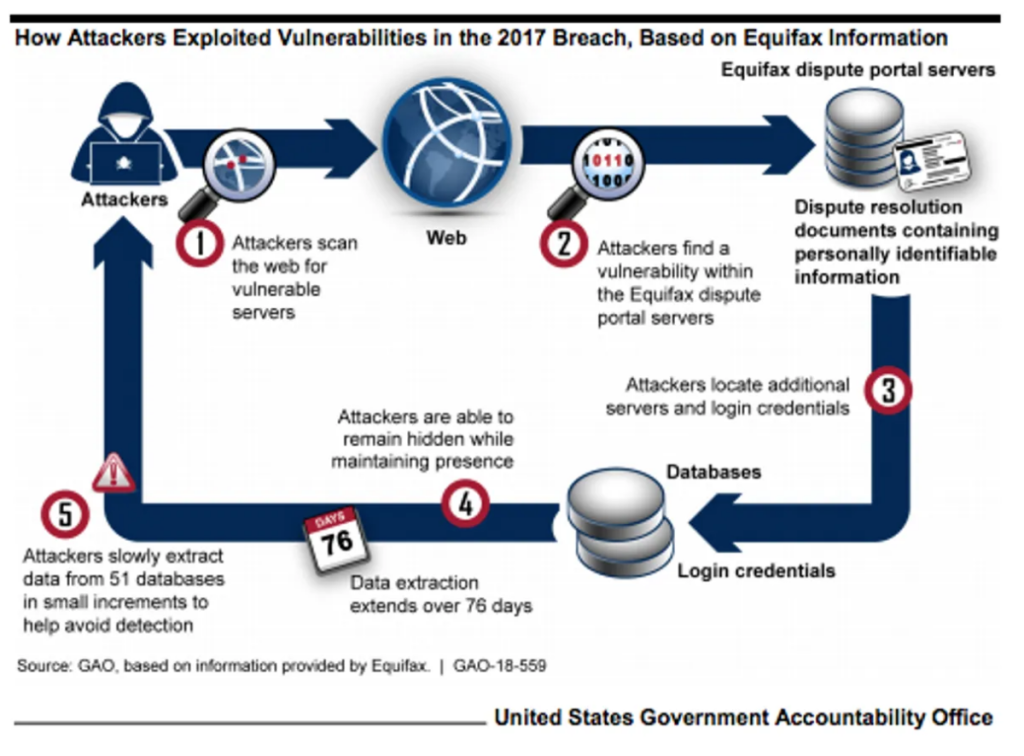
A data breach occurred when Equifax failed to update their servers with a security patch after they were alerted to its existence. Equifax was using the open-source Apache Struts framework to handle credit disputes from consumers. Security experts have found a group of hackers that are trying to find websites that have not updated their Apache Struts framework to the latest version as early as March 10, 2017 so that they can hack into their systems.
According to a report issued by Cnet tech, the hackers spent 76 days in the company’s network before they were detected. The thieves stole data piece by piece from 51 databases so they wouldn’t raise any alarms.
It took Equifax more than 2 months to discover its systems had been breached, and it blocked the hackers’ access three days after it found out. Since then, Equifax has implemented a new management system to handle vulnerability updates and verify that the patch has been applied.
5. Yahoo
This major hack of Yahoo’s email system occurred in August 2013. The company acquired by Verizon Communications stated that yahoo email users were affected by cyber attacks.
A spear-phishing email was sent in early 2014 to a Yahoo company employee, tricking the person into clicking on a link. The number of employees who were targeted and how many emails were sent has not been reported, but it only takes one person to fall for a trick like that.
Aleksey Belan, a Latvian hacker, searched Yahoo’s network for two items: its user database and the Account Management Tool, which is used to edit the database. He soon found them.
He wanted to make sure no one would cut off his access to the email service, so he installed a backdoor on a Yahoo server that would allow him access. And in December 2014, he stole a backup copy of Yahoo’s user database and transferred it to his own computer.
The database included names, phone numbers and recovery questions and answers for each account.
The account management tool didn’t allow text searches of user names, so hackers turned to recovery email addresses. Sometimes they identified targets by their recovery email address.
Throughout the process, Belan and his colleague had an air of professionalism about them. They generated cookies for only 6,500 of the approximately 500 million accounts they potentially had access to.
In the yahoo FAQ and press release, Yahoo has reported that, hackers stole data associated with more than one billion user accounts. This is separate from the incident which impacted 500 million user accounts. It was reported that the stolen data included names, email addresses, dates of birth, hashed passwords, and security questions and answers. It is also reported no payment card or bank account details were stolen.
6. Github
In February 2012, the GitHub hosting service centre was hit by a DDoS cyber attack of up to 1.35TB per second. This Github attack exploits a server running a memory caching system. Attackers use IP Spoofing, which aims to make fake requests on UDP servers. When UDP responds to a request, the UDP server will prepare the requested resources. If there are many phoney request attacks that enter the UDP server, then the system will be overloaded and will be used for attacks. However, GitHub got through this DDoS attack and was only inactive for 5 minutes.
7. Colonial Pipeline Ransomware Attack
The Colonial Pipeline ransomware attack, carried out by the DarkSide group, was one of the most notable cybercrime incidents in 2021. DarkSide, a ransomware-as-a-service (RaaS) group known for its sophisticated tactics, targeted Colonial Pipeline, a major fuel pipeline operator in the United States.
The attack took place in May 2021 and had far-reaching consequences.
The hackers gained unauthorised access to Colonial Pipeline's IT systems and deployed the ransomware, which effectively encrypted critical data and systems, rendering them inaccessible. In response, the company took the precautionary measure of temporarily shutting down its pipeline operations to contain the breach and prevent further damage. The pipeline, which spans over 5,500 miles and supplies nearly half of the fuel consumed on the East Coast of the United States, was offline for several days.
The impact of the attack was significant and led to fuel shortages across various states along the East Coast. Panic buying and hoarding exacerbated the situation, causing long lines at gas stations and price spikes. The disruption affected individual consumers and had consequences for businesses relying on a steady fuel supply, including transportation companies, airlines, and emergency services.
In coordination with law enforcement agencies and cybersecurity experts, Colonial Pipeline worked to restore operations and mitigate the effects of the attack. They engaged with the DarkSide group and reportedly paid approximately 75 Bitcoin or USD$4.4 million a ransom to obtain a decryption tool and restore their systems. While controversial, this decision was made to expedite the recovery process and minimise the impact on fuel distribution..
On June 7, 2021, the U.S. Department of Justice released a statement revealing its successful seizure of 63.7 Bitcoins from the initial ransom payment. However, due to the decline in Bitcoin's trading price since the time of the ransom payment, the recovered Bitcoins were valued at only $2.3 million. The FBI was able to retrieve the Bitcoin by possessing the private key of the ransom account, although it did not disclose the method through which it obtained the private key.

The incident highlighted the vulnerabilities within critical infrastructure sectors, emphasising the potential consequences of cyberattacks on essential services. It also raised concerns about the growing sophistication and capabilities of ransomware-as-a-service groups like DarkSide, who leverage advanced tactics and techniques to maximise the effectiveness of their attacks
8. The Accellion Data Breach
The Accellion Data Breach was a significant cybersecurity incident when threat actors targeted the Accellion File Transfer Appliance (FTA) software. This breach resulted in data breaches affecting multiple prominent organisations across the globe. Attackers exploited vulnerabilities present in the legacy FTA software to gain unauthorised access to sensitive data.
According to Reuters, Accellion has agreed to a settlement of $8.1 million to resolve a class-action lawsuit stemming from a data breach in December 2020. The breach occurred due to the exploitation of zero-day vulnerabilities found in Accellion's File Transfer Appliance (FTA). This incident had a significant impact, affecting millions of individuals at the time.
The Accellion FTA software, designed to facilitate secure file transfers, became the focal point of the attack. Exploiting the identified vulnerabilities, threat actors bypassed security measures through fraud software updates and gained unauthorised entry into the systems that utilised this software. Once inside, they were able to access and exfiltrate sensitive information.

Numerous high-profile organizations across various sectors fell victim to this breach, which had severe consequences for data privacy and security. The stolen data encompassed a range of sensitive information, including customer data, intellectual property, financial records, and other proprietary information.

The Accellion Data Breach underscored the importance of promptly patching software vulnerabilities and maintaining up-to-date security measures. In response to the incident, Accellion took steps to address the vulnerabilities and released patches to mitigate the risk. Organizations that were affected by the breach initiated incident response protocols to contain the damage, assess the extent of the breach, and notify affected individuals as required by applicable data breach notification laws.

Incidents like the Accellion Data Breach highlight the ongoing need for organizations to prioritise cybersecurity practices, including regular security assessments, timely software updates, and the implementation of robust security protocols. Proactive measures are essential to protect sensitive data, mitigate the risk of breaches, and maintain the trust of customers and stakeholders.
In the aftermath of the breach, organizations affected by the Accellion Data Breach often offered support to affected individuals, such as identity theft protection services and resources for securing personal information. They also took steps to reinforce their cybersecurity defenses and reevaluate their file transfer practices to prevent similar incidents in the future.
The Accellion Data Breach serves as a reminder of the evolving threat landscape and the importance of ongoing vigilance in maintaining strong cybersecurity measures. Organizations should continually assess and enhance their security strategies to mitigate risks and protect sensitive data from determined threat actors.
