What is Malware?
Malware, short for malicious software, is any computer software designed to damage or compromise the integrity of a system within a computer, phone or other electronic devices without the owner's consent. Malware can take many forms, including trojan horses, worm, adware, viruses, botnet, exploit, virus, and spyware.
Malware is typically delivered through email as a link or file. When someone clicks on the link or opens the file, the malware executes on their computer. Malware has existed since the Creeper virus first appeared. Since then, hundreds of thousands of different malware variants have been created with the intent of causing disruption and damage.
History of Malware
John von Neumann, a 20th-century Renaissance man, delivered a lecture on self-reproducing automata in 1949. However, the history of modern viruses begins with Elk Cloner in 1982, a program infected Apple II computers spread via floppy disks.
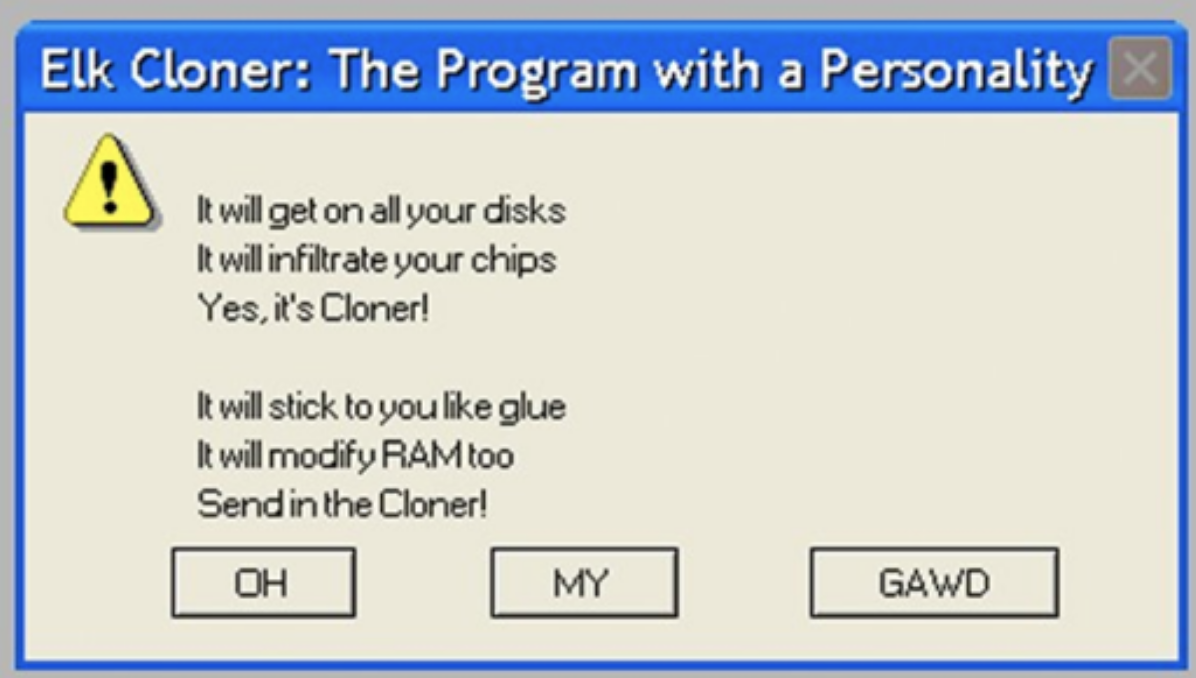
Cloner’s virus has been recorded as the first large-scale computer virus outbreak to occur, as the virus spread to all disks attached to a system. Although the program itself was harmless, its virulence is still considered the first large-scale computer virus outbreak in history. (Note that this occurred before any Windows PC malware.) Since then, viruses and worms have become widespread.
How does Malware spread?
Malware can take many forms, and each strain is different. Some malware is delivered via email and arrives as a link or executable file. Others arrive via instant messaging or social media. Even mobile phones are vulnerable to attack. The key to fighting malware is to be aware of all vulnerabilities so you can set up an effective line of defence against it.
Why do cybercriminals use malware?
Malware consists of a wide range of malicious software, including viruses. Cybercriminals use a combination of social engineering, phishing and malware to trick people into revealing their personal data, which can then be used for identity theft or stealing sensitive/personal data from their victims' computers. Some cybercriminals provide MaaS services to criminals or hackers. MaaS is an acronym for "malware as a service", which refers to the illegal lease of software and hardware for carrying out cyber-attacks.
Are smartphones and tablets susceptible to malware?
Malware criminals have taken a liking to the mobile market; smartphones are sophisticated handheld computers that can provide a gateway into a treasure trove of personal information and valuable data for those seeking to make dishonest dollars.
Unfortunately, smartphone vulnerabilities discovered in the early 2000s have led to increasing malicious attempts to take advantage of those weaknesses. Malware can find its way onto your phone in several ways:
- Clicking on a dodgy attachment or URL link
- Downloading an unreliable app
- Get infected through emails, texts, fake wifi or Bluetooth connection
Unfortunately for all mobile users the list above are only a few examples, as cybercriminals are always coming up with new and maliciously creative ways to hack mobile software devices.
Cybercriminals find the mobile market attractive and can leverage their efforts because of its enormous size. The GSMA, a trade association for mobile carriers, in 2017 claimed that there are over 5 billion mobile device users worldwide. A quarter of these users own more than one device.
Mobile and portable devices are also an especially dangerous vector for malware because they go with us everywhere. The PC is no longer a personal computer; it's something that's shared by many people in the office or at home. Phones, on the other hand, are distinctly personal devices. The fear of losing your phone--a condition known as nomophobia--is a real thing and affects many people today.
How can I tell if my phone or tablet device is infected with malware?
You might notice some unusual behaviour if your smartphone or tablet device is infected. For example, you might see any of the following signs;
- A strange increase in data usage can be caused by malware that displays ads and sends out misappropriate information from your device.
- Mysterious simulated charges on your phone bill. This happens when malicious software makes calls and sends texts to premium numbers.
- Your device's battery runs down quickly. Malware can drain your system's resources, leaving your computer running slowly and consuming more power than usual.
- You suddenly see pop-ups with invasive advertisements. This could happen when you install something that hides adware. It's best if you don't click on these advertisements.
- Your phone is hot. That could be a sign that your phone is infected with malware. According to Kaspersky lab, the Loapi trojan is a type of malware that can make your phone work so hard that it overheats, bulging out the battery and leaving it dead.
- Wi-Fi and Internet connections can turn themselves on, even when you don't want them to. Malware can spread by ignoring your preferences and connecting to the Internet without your knowledge.
Are personal computers susceptible to malware?
Malware can get onto your computer in two main ways: through the Internet and email. A lack of anti-malware security software puts your computer at risk of being infected with viruses.
Malware can get onto your computer in several different ways, including;
- Visiting hacked websites
- Viewing malicious ads on legitimate sites
- Downloading infected files
- Installing programs from unfamiliar sources
- Opening email attachments from unknown senders
Malware can hide in seemingly legitimate applications, especially when downloaded from unknown websites or direct links (in an email, text, or pop-up ad) instead of an official app store. It is essential to look at the warning messages when installing applications and read the entire description before downloading an app.
How can I tell if my computer is infected with malware?
When you have malware on your computer system, it can cause many different types of problems. Here are some signs that you may have malware:
If your computer starts slowing down, It might be because of malware. One effect of malware is to use up system resources even when you're not using the Internet or other applications. For example, a computer that's been roped into a botnet tends to have its fans whirring at full speed because something is taking up resources in the background while you work.
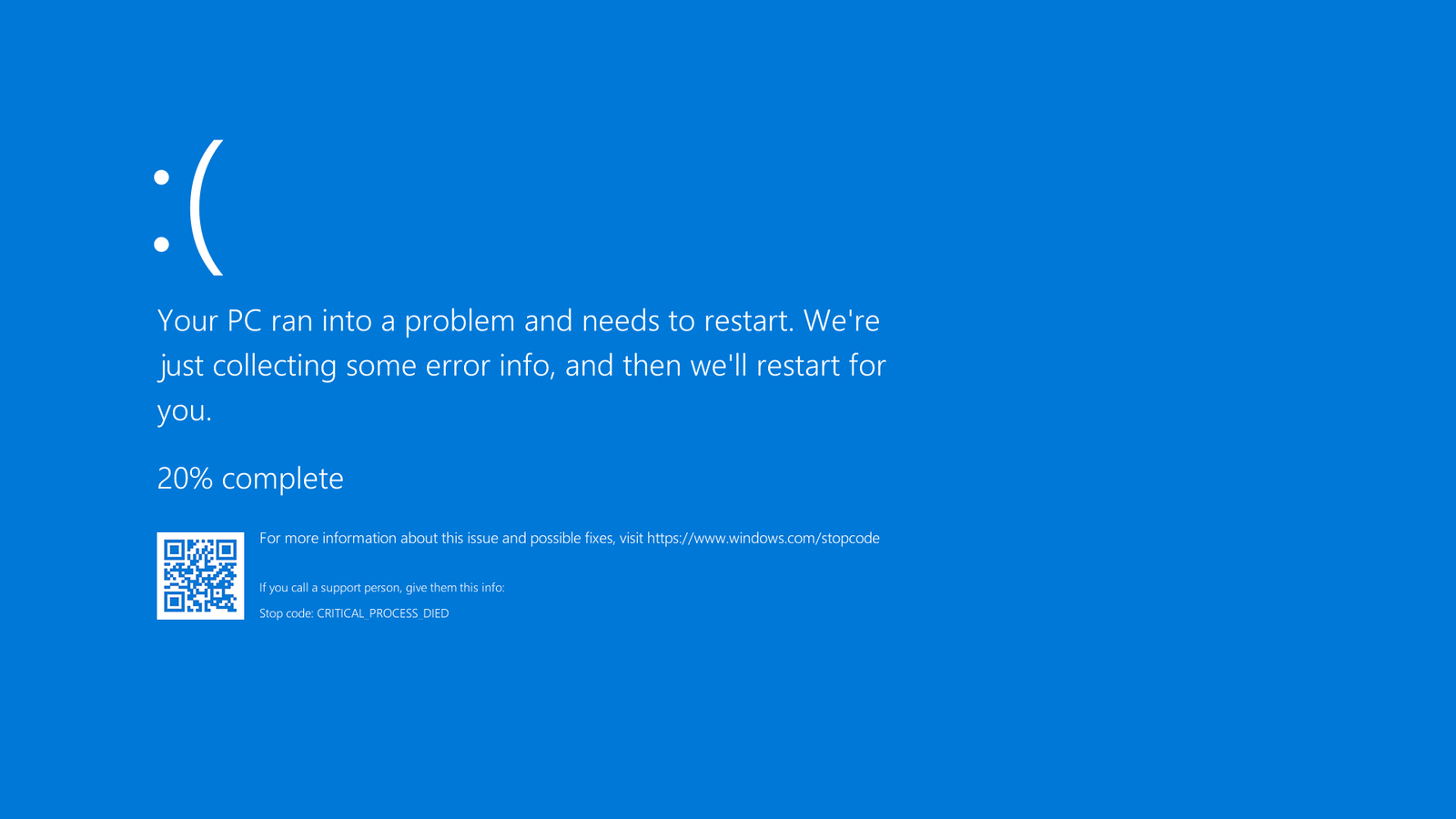
Your computer crashes. This can be a freeze--when your screen stops responding to your commands--or a BSOD (Blue Screen of Death), which appears on Windows systems after encountering a fatal error.
You have an ad-filled screen with pop-ups that won't go away. These are typical signs of malware infections. Pop-ups are usually associated with a form of malware called adware. What's more, most pop-ups come packaged with other hidden threats. If you see something akin to "CONGRATULATIONS! You have won $1000!", do not click on it. Whatever free prize the ad promises will cost you plenty.
A mysterious shortage of disk space has been detected. This could be due to a program attempting to access more space than you might be unaware you are allowing.
Your antivirus product stops working, and you have difficulties turning it back on. Sneaky malware infects your computer and may disable your antivirus settings leaving you exposed to vulnerabilities.
If your computer is locked and you see a ransom note on your desktop, you might be a victim of ransomware. Ransomware is a type of malicious software used by cybercriminals that locks you out of your computer and demands payment in exchange for decrypting the data or gaining back access.
Types of Malware
Cybercriminals use a variety of malware to steal information, demand ransoms or commit other crimes. The following is a list of common types of malware;
*(Click on the images to find out more about the following types of malware.)
Similar to how soldiers hid in giant horses during ancient Greece, Trojan Horse malware can hide within or disguise itself as legitimate software. Acting discreetly, this type of malware will create backdoors that give other variants easy access.

Worms are named for how they spread. They start from one infected machine and weave their way through the network to connect with consecutive devices to continue the spread to other devices. This type of worm malware can quickly infect entire networks of devices if no action is taken.

An exploit is a code that takes advantage of a security flaw or vulnerability, allowing an attacker access to a system. A friendly party may release an exploit as a proof-of-concept, while an unfriendly party may use it in their operations.
Adware is software that shows ads within an application, browser, or operating system. These ads may include pop-ups, banners, and videos. In most cases, free software is most likely to contain adware when developers don't charge directly for products and services but earn revenue from advertising.
A botnet is a group of computers infected by malware and controlled from one central point (known as a bot herder). From this central point, the attacker can send commands to every computer on its botnet to coordinate criminal action.

Viruses are one of the most common types of malware, software designed to gather sensitive information, access personal computer systems, or disrupt computer operations. Like a biological virus, it can spread, causing fatal damage to the core systems and corrupting files. A virus attaches its malicious code to clean code and waits for an unsuspecting user or an automated process to execute it.
Spyware is malware that secretly collects information from someone's computer without the owner's consent. Such as passwords, credit card details, and other sensitive information.
Protecting yourself from malware
Given the detrimental of a malware attack and the increasing popularity of ransomware, here are some tips for protecting your computer and devices from malware;
Be aware of digital security. Whether you're commuting for business or pleasure, it's crucial for today's world. Learn about digital security and make sure to practice good habits while you are on the go.
Ensure you have the latest security updates installed, keep your software up-to-date and centrally manage it. You can also expedite this process by launching updates manually or setting auto-update for every software through its settings. Patches are updates to the software that fix bugs and provide enhanced security features. Microsoft releases security updates every second Tuesday (Patch Tuesday) of each month, and much other legitimate software has followed this implementation. To learn more about these updates, read overt's Patch Tuesday article.
Be sure to back up all your data. This goes for all the endpoints on your network and network shares. With backups in place, you can always wipe and restore an infected system from a backup.
Wi-Fi networks are a prevalent access point for cyber attackers. When working in public, it is essential to avoid using public networks. You will most likely use your organisation's network when working in the office. However, if you use work devices outside of the office, use a VPN or ensure you are connected to a secure Wi-Fi network.
Maintaining a good security system in your computer and your personal life is essential. Along with a firewall on your computer, you should also implement and maintain an effective "human firewall." A human firewall is a collection of best practices to support effective cyber security. Learn more about how to upgrade your "Human Firewall" through Overt's 12 non-technical security tips.

By following all these steps, you will be in much better shape to keep your cybersecurity strong personally and digitally.



