What is computer exploit vs malware
An exploit is a program consisting of malicious codes that takes advantage of a weakness in a system or application to gain access to the application or data. Exploits target applications, but vulnerabilities are the weaknesses that make exploits possible. Once the hacker gains access to their victim’s computer, the hacker will install viruses such as ransomware, adware, or viruses.
Malware is the derogatory term for a computer virus that can wreak havoc on your system. Unlike malware, exploits are not inherently malicious and can be used to achieve legitimate goals. However, they are still likely to be used for nefarious purposes, including stealing data and spying on users.
How computer exploit works
A computer exploit can be in the form of software or code that identifies security flaws in applications, systems, and networks and takes advantage of them to benefit cyber criminals.
Hackers may send phishing emails to trick potential victims into visiting these websites. As a rule, most exploits target commonly installed browser plugins like Microsoft Silverlight, Adobe Flash, Java or Internet Explorer (which was discontinued by Microsoft in 2016).
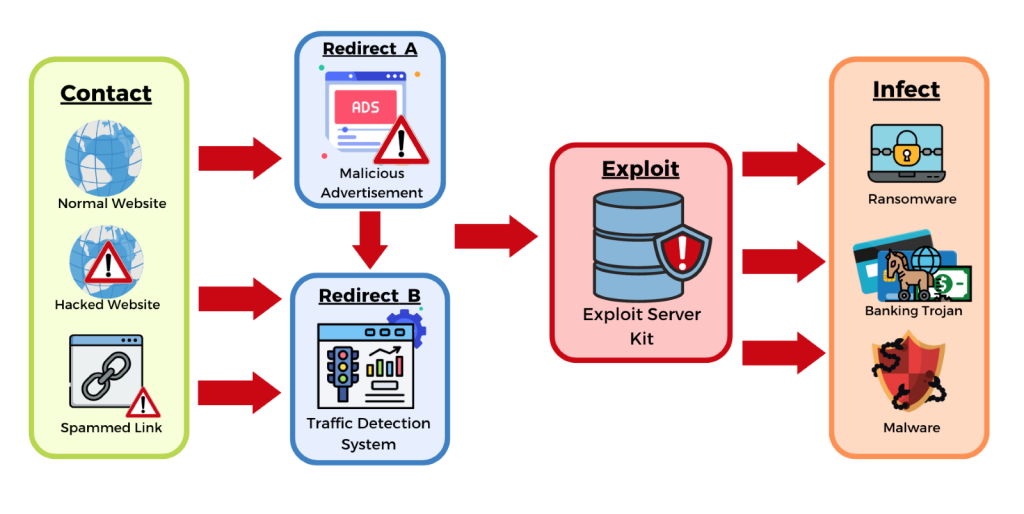
-
- First, cyber criminals trick people into visiting an exploitative website by sending them spam email, pop up advertisements or other socially engineered messages.
- Second, the exploit kit looks for weaknesses in software installed on the systems and devices used to access the link.
- Third, an attacker will use the vulnerability to gain access to your system or device.
- Fourth, a piece of malicious software, or payload, is installed and activated.
Computer exploit categories
All computer exploits are organized into the following main two categories: known and unknown exploits.
-
- Known exploit is an attack that has already been discovered by cybersecurity researchers. If a known exploit affects the software or hardware on your computer, you can download the latest version of your operating system or program to plug the hole. For example, when Moodle (a piece of LMS software) has a vulnerability, the known exploits are the ones that the cyber security specialists have discovered. Once a vulnerability has been found, software developers can make patches and updates to fix these holes.
- Unknown exploit could either mean that cybercriminals are the only ones aware of the flaws targeted by these exploits or that software developers couldn’t create a fix for this issue as fast as hackers could build a corresponding exploit kit. Zero-day unknown exploit are always on the lookout for user reports on the most recently detected security flaws before developers can analyse them and create a patch.
Some unknown exploits even take advantage of software that is not supported anymore, as developers are unlikely to release fixes for such products.
What is Exploit Kits?
When software is developed, vulnerabilities are defined as the errors or flaws within the software’s code. Cybercriminals and malicious developers can take advantage of these vulnerabilities to access the software and the connected devices. To do this, malicious developers create “exploit kits”, which are collections of exploits often bundled with other software. Exploiting the software leaves holes in the software’s built-in security and allows viruses, ransomware, or other malware infections to infect the victim’s device.

As shown in the illustration above, the middle window is locked, so there’s no vulnerability. The window on the right is open and vulnerable, but too high up to exploit. The window in the left corner is open and vulnerable and close enough to the ground to exploit.
List of advanced computer exploit kits
Many cyber criminals are using exploit kits to distribute malware and ransomware. These kits are highly automated, making them easy for criminal groups to use as a distribution method. They are not only used for mass malware distribution but also for RATs (remote access trojan) like Poison Ivy and Mars Stealer that allow access to user data without their knowledge.
Here are some examples of the types of exploits kits cybercriminals use to attack vulnerabilities in systems;
Rig Exploit Kit
The rig is a type of malware that uses the security flaw in Microsoft’s Internet Explorer browser. The malware guides the victim to a malicious website that delivers the RIG exploit kit, which can be used to steal important information and download other malware like ransomware. A new VIP version of the RIG exploit kit was discovered in 2016, with new URL patterns that are different from previous versions.
According to a report by Malwarebytes, in 2017, cybercriminals hacked websites to distribute ransomware known as PrincessLocker via drive-by downloads. The campaign uses compromised websites and the RIG exploit kit to deliver PrincessLocker (also known as Princess), a strain of malware. PrincessLocker uses the same template as the popular ransomware variant Cerber, but their internal codes are very different.
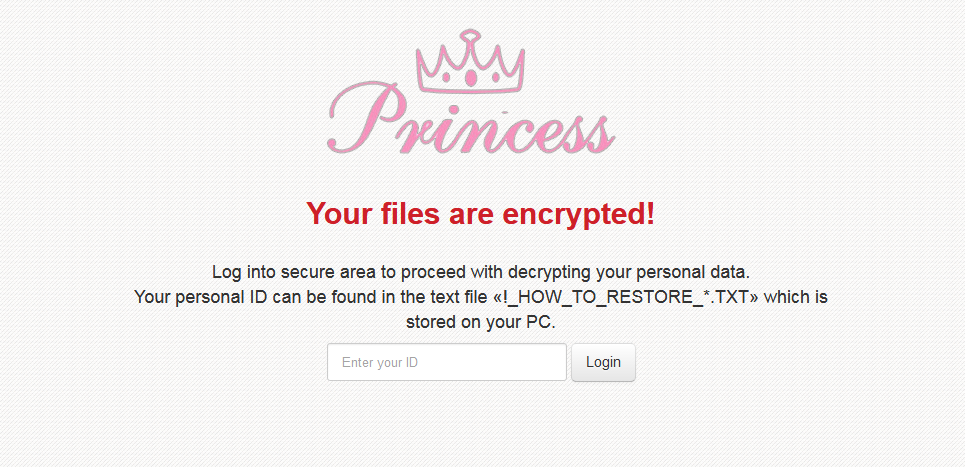
It’s possible that PrincessLocker’s creators are not as experienced with coding. But in this campaign, the cybercriminal injects an iframe that redirects from the compromised site to a temporary gate. The call to the RIG exploit kit landing page is done via a standard 302 redirect that leads to one of several Internet Explorer or Flash Player vulnerabilities. To decrypt their files, victims are asked to pay a ransom of 0.0770 Bitcoins, or about $367. If they do not pay within seven days, the price will increase to 0.1540 Bitcoins, or about $738.
GreenFlash Sundown Exploit Kit
GreenFlash Sundown is an advanced exploit kit that was first observed in 2015. It is used in the ShadowGate malware campaign. When a user visits a site with these adverts, Greenflash Sundown will identify their system before deploying a suitable exploit. If successful, it will attempt to install and execute RC4 encrypted payloads.
Since the beginning, when the GreenFlash Sundown exploit was released, it has been delivering spyware, mysterious ransomware tools, and several secondary payloads, including cryptocurrency miners.
On March 27, 2018, researchers detected a variant of Hermes ransomware spreading via a compromised Korean website. Security experts initially suspected malicious JavaScript code but later found that the code was embedded directly into the main page’s HTML source code.

The Hermes virus first hit the Internet in October 2017. At the time, it used a combination of AES and RSA cryptography and added a “.hermes” file extension to the targeted files on the affected computer. In October 2017, cybercriminals were held responsible for a security breach at the Far Eastern International Bank in Taiwan. They attempted to wire as much as $60 million to banks in the United States, Cambodia, and Sri Lanka.
The hacker group was not only stealing money from banks but continued to update their ransomware virus. A couple of months later, hackers started distributing an updated version of the ransomware. In April 2017, researchers reported Hermes 2.0, similar to the first virus. Hermes 2.0, the cyber criminal’s updated file-encrypting malware, targets users in South Korea. And all that is only possible with the help of using the GreenFlash Sundown exploit kit.
Magnitude Exploit Kit
Magnitude exploit kit, or Malvertising (in short for malware advertising), is a form of online advertising fraud that attempts to disguise the advertisements and their associated tracking code. One widely used technique for malware distribution is through compromised networks or websites, designed to look like legitimate sites and pop up advertisement but are actually owned by criminals.
Formerly known as PopAds, magnitude is one of the most frequently seen and the oldest exploit kits. Malicious advertisements can be spread through online advertising networks, including reputable website such as Yahoo! ‘s advertising network. In 2013, security researchers discovered that Yahoo! was one of the top advertising networks being abused by cybercriminals to spread malware throughout the Internet.
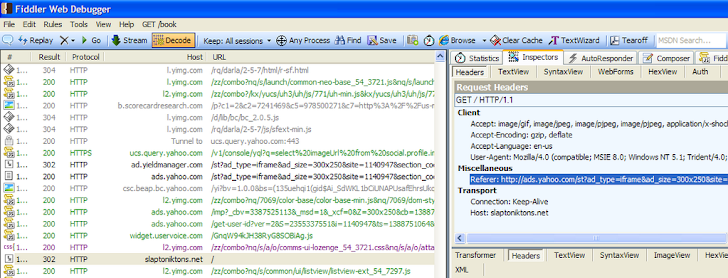
Hackers use Yahoo’s servers to distribute malware that infects users’ computers and steals personal information. Malicious advertisements have been served through ads.yahoo.com, providing hackers an easy way to reach hundreds of thousands of people visiting Yahoo’s site. More than 300,000 users per hour were redirected to malicious websites serving the ‘Magnitude Exploit Kit’. The exploit kit installs malware such as Necurs, ZeuS, Andromeda, advertisement clicking malware and Ngrbot.
Fallout Exploit Kit
The Fallout Exploit Kit has been used to deliver multiple types of ransomware, including GandCrab and Tescrypt.
In September, Proofpoint discovered that cybercriminals were distributing the DanaBot banking Trojan in spam campaigns. The DanaBot malware was first found in May 2018 and targeted Australian banks, but soon DanaBot was adopted by cybercriminal groups that targeted European banks. Cybercriminals have sent hundreds of thousands of spam emails imposed as “digital faxes” containing links to a document with a malicious macro to install the Hankitor dropper.

The Hankitor dropper downloads and installs the Trojan, several other attackers’ tools, and DanaBot malware.
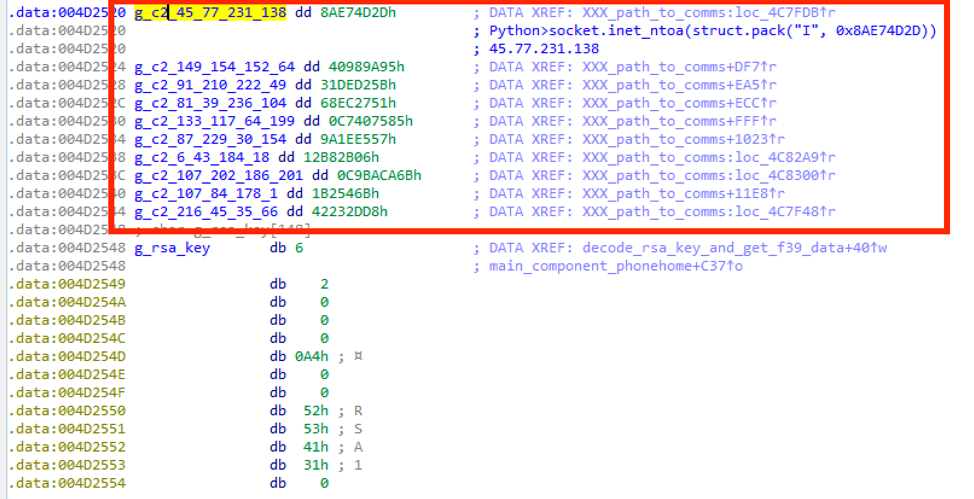
Groups of cybercriminals are distributing malware through spam and phishing campaigns. This particular cybercriminal group uses the Fallout Exploit Kit. DanaBot is modular malware written in Delphi, capable of injecting malicious scripts into various applications. One of its modules installs a TOR proxy and enables access to “.onion” websites.
Possible takeaway: Computer exploits are dangerous, but it is avoidable.
Exploits are dangerous and can harm your computer. But all these vulnerabilities and exploits are avoidable. Users must be aware of potential dangers associated with exploits and malware implementations to protect themselves from malicious attacks and viruses.
Update your browsers and plugins to their most recent version, and switch on your firewall for security, prevention, and protection against vulnerability exploits. With this information, you should have a better understanding of how exploits work and what they can do. Check out Overt software solution’s top 12 non-technical security tips to ensure you have the extra protection and upgrade your human firewall.

