What is Multi-factor authentication (MFA)?
Multi-factor authentication (MFA), also known as two-factor authentication (2FA), is a digital security strategy that requires multiple independent identification methods to verify your identity. Multi-factor authentication combines 2 or more categories of credentials:
- Something you know (such as a username and password)
- Something you have (like a security token)
- Something you are (such as biometric verification methods)
The purpose of multi-factor authentication is to make it more difficult for cybercriminals to gain access to their targets, such as a physical location or database. Thus, when one-factor authentication is compromised, the attacker still needs to hack or breach one or more barriers before successfully accessing the target’s device or account.
Multi-factor authentication decreases the possibility of being compromised by cyber attacks and is a core component of any identity and access management framework.

*Find out more about how Overt’s Multi-factor authentication (MFA) works
How does Multi-factor authentication (MFA) authenticate?
MFA authentication factors are categories of credentials used for identity verification. Each additional authentication factor increases the assurance that an entity involved in some kind of communication or requesting access to a system is the one it claims to be.
Credentials consist of 3 factor categories where 2 or more credential factors are combined as a MFA authentication. Here are the 3 categories of authentication factor;
Knowledge-based authentication (KBA)
Knowledge-based authentication (KBA), is the type of credential authentication in which the system asks for a piece of personal information that only the person being authenticated should know. As its name suggests, KBA is based on some sort of knowledge that only you would know. If your identity can be proved by this knowledge, you will be granted access.
Inherence authentication
Inherence factors verify someone’s identity based on a feature that is unique to them, such as their fingerprint or thumbprint. Other examples could include voice and facial recognition, and retina scans.
Using biometrics to identify users can be a very secure form of authentication, as biometric data is unique to each individual. However, if a system requires a fingerprint scan to access it can only be accessed on devices with hardware that supports that specific authentication factor. This restriction can be useful for security while at the same time negatively impact user convenience.
In this instance, account username or e-mail address’ are not considered as an secondary authentication factor because this is how a user initially claimed their identity to the system.
Possession authentication
Possession factors are designed to grant access to a system only to a specific user. Possession factors are usually controlled through a device or separate account known to belong to the correct user. Here is how the possession factor works;
- You can sign up for an account by providing a password, email and phone number.
- You logged in to the account with the username and password you used when signing-up.
- When you press the “enter” button to request system access, a one-time password is generated and sent to your registered mobile phone number or email address.
- Then you enter the generated “one-time” password and gain full access to the system.
- One-time passwords can be generated automatically and sent to the user’s cellular device via SMS or a third-party mobile app. Only the right owner/user can access the system if he has the proper device in his possession.
Multi Factor Authentication Alternatives
Token Authentication
Token authentication is one of many methods that can be used as an authentication factor. This method can be used on a smartphone to show an image to your webcam or play a sound which can be compared to an original. As this is not a very strong authentication method (for now), token authentication is advisable to be used with another factor and not as the sole factor.
Single sign-on (SSO)
Single Sign On (SSO) is a method used to provide access to several resources after the user has been authenticated once. The idea is that once the user has been identified and approved, the SSO software provides access to all platforms tied to the SSO. An SSO system will usually require multi-factor authentication (MFA) when logging in, as a safeguard against breaches.
Time-based One-time Password (TOTP)
Time-based One-time Password (TOTP) is a special authentication method that uses a one-time code based on the time. The server and the user both run simultaneous calculations with the same seed and time-stamp. If the results match, the user is granted access. Obviously, this authentication method should be used with other factors in any login procedure, as losing your machine or any other way that reveals the algorithm could allow access to others.
How can Multi-factor authentication (MFA) help protect your organisation while on vacation?
Especially for organisations, implementing multi-factor authentication (MFA) in the system is the best way to protect your business from cyberattacks. Plus, it’ll give you peace of mind while you’re on vacation because of the following benefits:
Saving and reducing management cost
Frequent password resets can burden your helpdesk. Multi-factor authentication reduces this burden by offering users a quick and secure way to reset their passwords. As you focus on meeting the needs of holiday shoppers or taking time off to be with loved ones, hackers are looking to exploit any vulnerabilities in your business’s system. The best way to protect your company from this kind of attack is to use multi-factor authentication (MFA). You can set up MFA on your eCommerce accounts and other platforms to better protect your business credit card information from being hacked or stolen.
Give extra protection against identity theft.
Based on research conducted by security.org, 68% of people use the same password across all of their accounts.
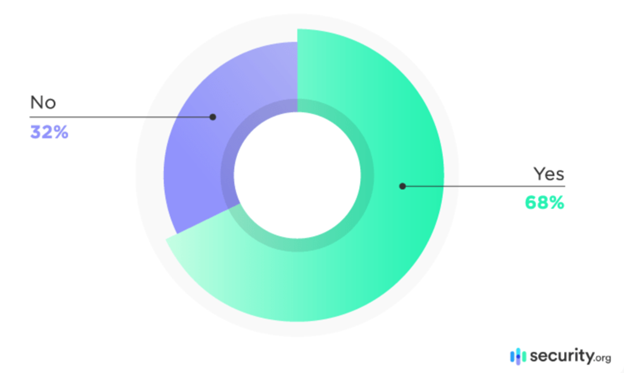
Attackers could steal your password by using pharming, phishing, or keylogging. If a hacker has your password, he can do many bad things with it. Multi-factor authentication (MFA) is a way to keep your data and systems safe because MFA helps prevent unwanted incidents by requiring 2 or more-factors of authentication. …
Before the holidays, take a few minutes to consider your account security. Using these best practices, you can minimise the possibility of having your accounts compromised.
Overt Software Solution uses multi-factor authentication (MFA) to protect its platform.
Overt software solutions, secures its platform using a two-step verification process that incorporates the third-party Google Authenticator (for iOS and Android devices) and Authenticator (from Windows devices) applications.
Our commitment and security reputation to protecting user data are represented by our Cyber Essentials Plus Certified compliance and our recent achievement of ISO27001.
Now that you know about Multi-factor authentication (MFA), why not implement these factors to give your organisation some extra protection so you can rest assured while on vacation!? We are available 24/7, just for you. For further information about our MFA services, please contact our success team.
-
- Enable multifactor authentication (MFA) whenever possible. This security feature requires you to take an extra step to verify your identity before you can log in, and it could help keep your information safe if your account’s password is compromised.
- Be sure to use a different password for every online account. If you can’t manage that, at least create passwords for your financial accounts that are hard to guess. A password manager makes this easy to do
- Scammers are always on the prowl, but the holiday season is especially ripe for identity thieves and fraudsters. While the dangers are real, you can protect yourself from becoming a victim and prevent hackers from accessing your work device/ email while you’re on holiday and pretending to be you by following the tips mentioned above.
Extra protection with Single Sign-on (SSO) combination
Single sign-on (SSO) is a technology approach that allows you to use a single set of credentials across multiple applications. Using SSO reduces the number of cyber attack surfaces because users with access only log in once daily and only use one set of credentials. By combining both multi-factor authentication (MFA) with single sign-on (SSO) you will give your business multiple layers of protection.
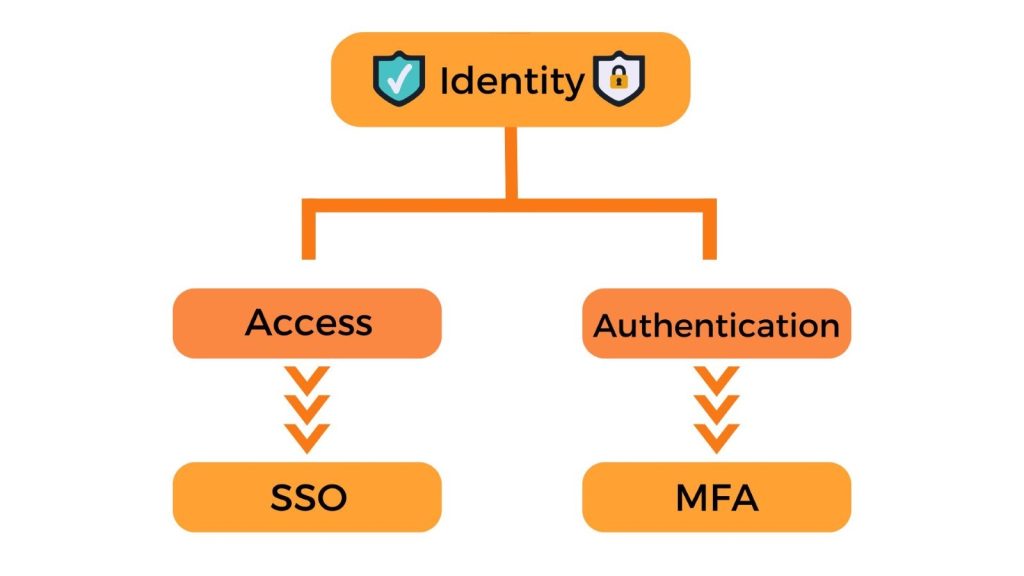
Enhancing your enterprise security means that you can enjoyyour drink while on vacation, knowing that your SSO and MFA are defending your organisation. Remember, where possible always challenge each login attempt with an extra layer of MFA protection.
Why is using MFA better than one-authentication factor?
One-step verification methods, like passwords, can be easy to hack. Sometimes this is because of user behaviour patterns and also due to the limitations of technology:
- A location-based authentication factor can be defeated by technologies that mask the source of network traffic, making it difficult to authenticate the origin accurately.
- A behaviour-based authentication factor can be observed by cyber criminals and easily replicated.
- Knowledge-based authentication factors, such as memorising passwords and PINs, can make it harder to remember the correct information and lead to users with overly simplistic passwords or those who don’t change them frequently. Thus, making it easier for hackers to guess and hack.
- Biometric and possession-based authentication factors can make it difficult for hackers to gain access to a network. Biometrics and possession-based authentication factors can be combined into a multi-factor authentication process, which decreases the likelihood of a hacker gaining unauthorised access to a secured network.
While you’re preparing for the holiday season, so are cybercriminals. Nearly 36% of age 45 – 54 and one-quarter (24%) of Americans have reported they’ve been victims of fraud, scam or identity theft during the holidays.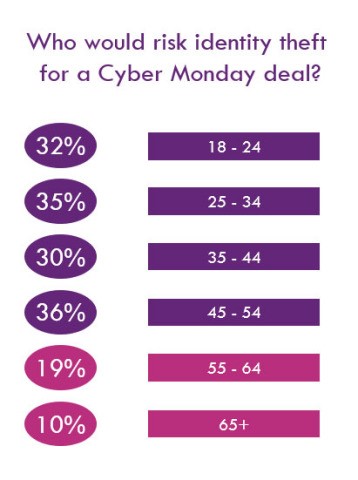 According to Experian, online users should be looking for helpful ways to protect their digital identities. You’ve probably heard all the basics for protecting your password—strong passwords and changing them often—but even these steps don’t provide ironclad protection.
According to Experian, online users should be looking for helpful ways to protect their digital identities. You’ve probably heard all the basics for protecting your password—strong passwords and changing them often—but even these steps don’t provide ironclad protection.
However, even when using authentication we advise that you do not become complacent about your cybersecurity because although MFA is stronger than having only one-authentication factor, MFA is not foolproof.
Overt Software Solution uses multi-factor authentication (MFA) to protect its platform.
Overt software solutions, secures its platform using a two-step verification process that incorporates the third-party Google Authenticator (for iOS and Android devices) and Authenticator (from Windows devices) applications.
Our commitment and security reputation to protecting user data are represented by our Cyber Essentials Plus Certified compliance and our recent achievement of ISO27001.
Now that you know about Multi-factor authentication (MFA), why not implement these factors to give your organisation some extra protection so you can rest assured while on vacation!? We are available 24/7, just for you. For further information about our MFA services, please contact our success team.
